Probe
Overview
This is an easy rated tryhackme room focused on active and passive enumeration techniques.
Initial Enumeration
I begin with an aggressive nmap scan targeting all ports on the server.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
root@ip-10-10-191-190:~# nmap -sT -T5 -A -p- 10.10.205.139
Starting Nmap 7.80 ( https://nmap.org ) at 2025-07-13 15:24 BST
Nmap scan report for ip-10-10-205-139.eu-west-1.compute.internal (10.10.205.139)
Host is up (0.00085s latency).
Not shown: 65527 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
80/tcp open http lighttpd 1.4.55
|_http-server-header: lighttpd/1.4.55
|_http-title: 403 Forbidden
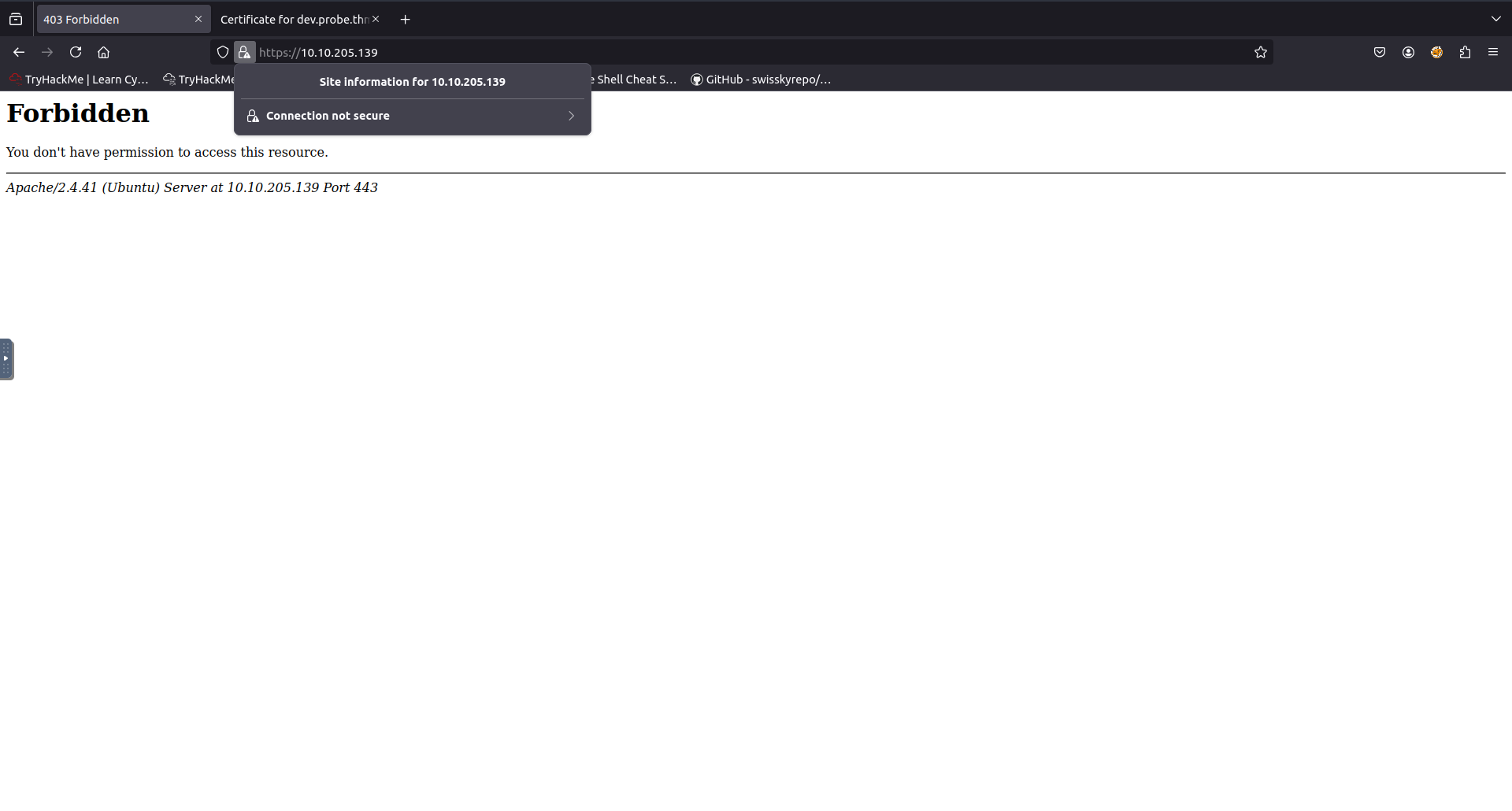
443/tcp open ssl/http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: 403 Forbidden
| ssl-cert: Subject: commonName=dev.probe.thm/organizationName=Tester/stateOrProvinceName=Some-State/countryName=US
| Not valid before: 2023-07-18T10:57:05
|_Not valid after: 2024-07-17T10:57:05
| tls-alpn:
|_ http/1.1
1338/tcp open ftp vsftpd 2.0.8 or later
1443/tcp open ssl/http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: PHP 7.4.3-4ubuntu2.19 - phpinfo()
| ssl-cert: Subject: commonName=dev.probe.thm/organizationName=Tester/stateOrProvinceName=Some-State/countryName=US
| Not valid before: 2023-07-18T10:57:05
|_Not valid after: 2024-07-17T10:57:05
| tls-alpn:
|_ http/1.1
1883/tcp open mqtt
|_mqtt-subscribe: ERROR: Script execution failed (use -d to debug)
8000/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
9007/tcp open ssl/http Apache httpd 2.4.41 ((Ubuntu))
|_http-generator: WordPress 6.2.2
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Welcome to my Blog – I am going to be the best blogger
| ssl-cert: Subject: commonName=myblog.thm/organizationName=Internet Widgits Pty Ltd/stateOrProvinceName=Some-State/countryName=US
| Not valid before: 2023-07-08T11:01:57
|_Not valid after: 2024-07-07T11:01:57
| tls-alpn:
|_ http/1.1
MAC Address: 02:BE:FB:3F:46:9F (Unknown)
Aggressive OS guesses: Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), Linux 3.10 - 3.13 (94%), Linux 3.8 (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Linux 2.6.32 (92%), Linux 2.6.39 - 3.2 (92%), Linux 3.1 - 3.2 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.85 ms ip-10-10-205-139.eu-west-1.compute.internal (10.10.205.139)
From this i can see that the version of apache running is version 2.4.41. I can aso see that an ftp server is running on port 1338. Additionally an ssl certificate was discoverd with a FQDN of dev.probe.thm. Visiting the https webserver running on port 443 displays a pop up stating that this is a self signed certificate accepting this risk and continuing displays the following.
From here we can click on connection not secure and then more information and then view certificate this will display the following.
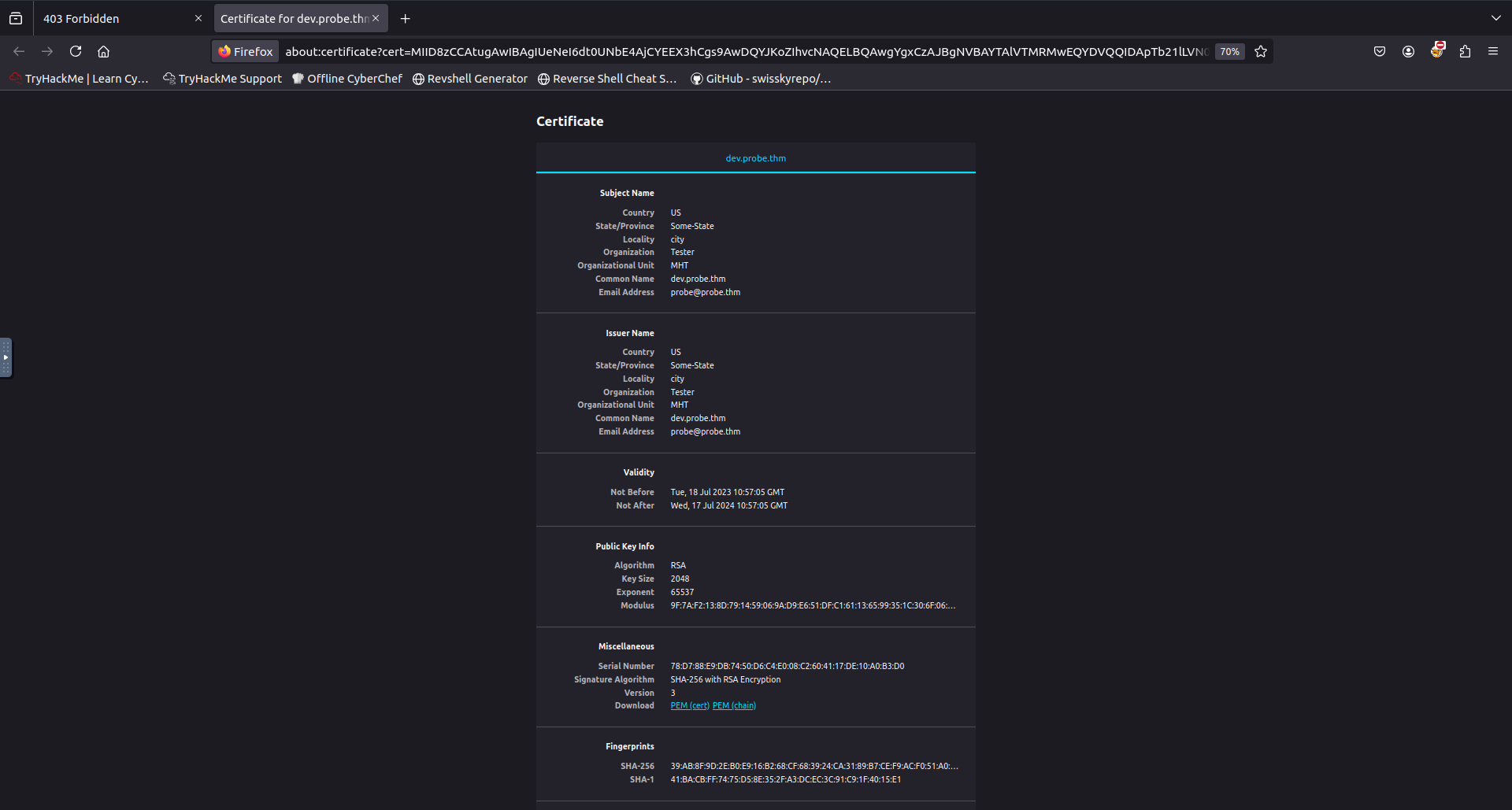
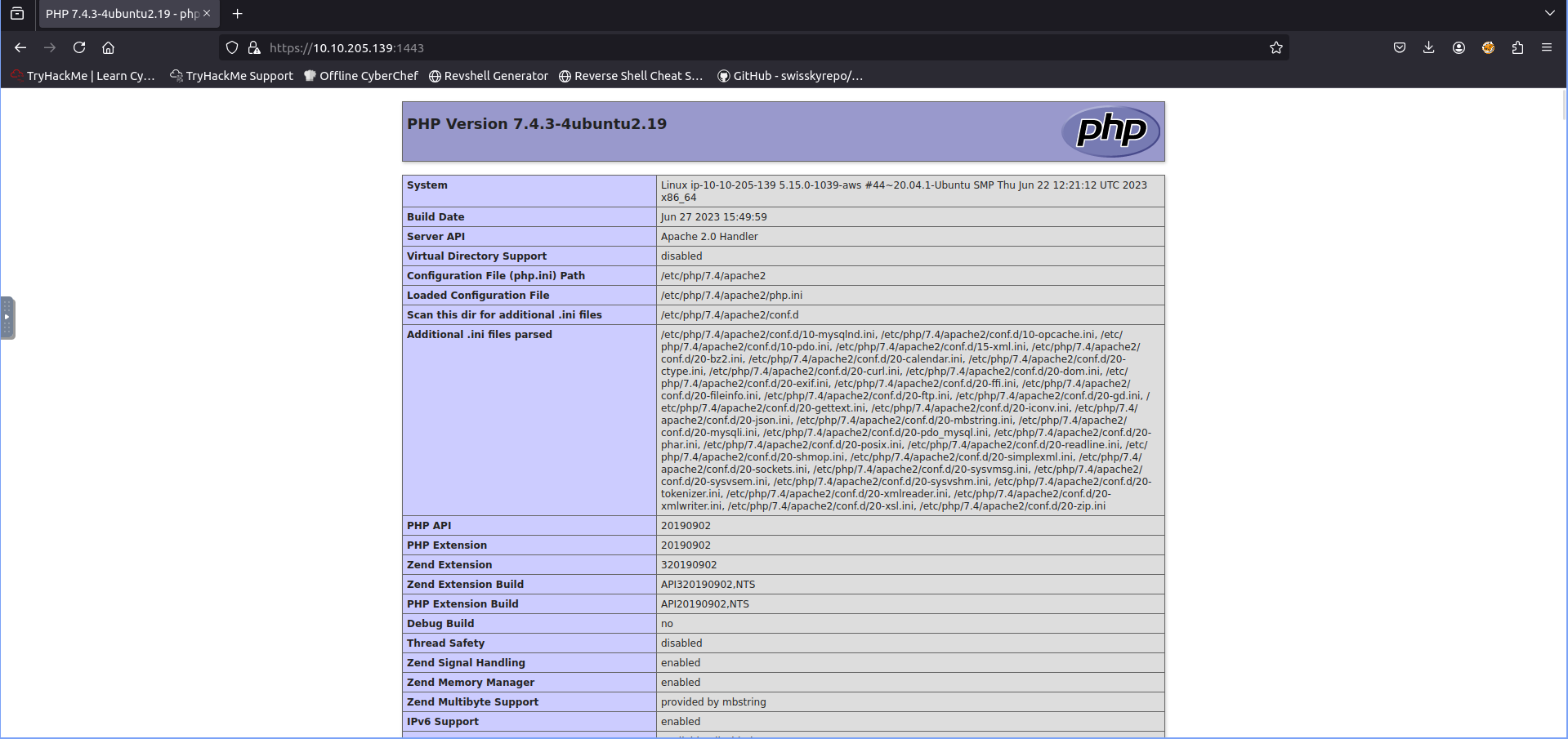
We can clearly see now that the email address registerd to the certificate is [email protected]. I then began checking out the other ports and found on port 1443 a php version page revealing that the server was running php with extension build of API20190902,NTS.
After this i then connected to the ftp service running on port 1338 i used the below command to achieve this.
1
2
3
4
5
root@ip-10-10-191-190:~# telnet 10.10.205.139 1338
Trying 10.10.205.139…
Connected to 10.10.205.139.
Escape character is '^]'.
220 THM{WEL********113}
In the FTP banner there was a flag. Now we need to find out what database the server is using to do this i first began looking at nmaps previous output to see if there was anything i missed i found nothing i then used gobuster to scan for directories on each webserver starting with the http server on port 8000. Below is the command i used.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
root@ip-10-10-191-190:~# gobuster dir -u http://dev.probe.thm:8000 -w /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://dev.probe.thm:8000
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 280]
/.htaccess (Status: 403) [Size: 280]
/.htpasswd (Status: 403) [Size: 280]
/contactus (Status: 301) [Size: 325] [--> http://dev.probe.thm:8000/contactus/]
/index.php (Status: 200) [Size: 0]
/javascript (Status: 301) [Size: 326] [--> http://dev.probe.thm:8000/javascript/]
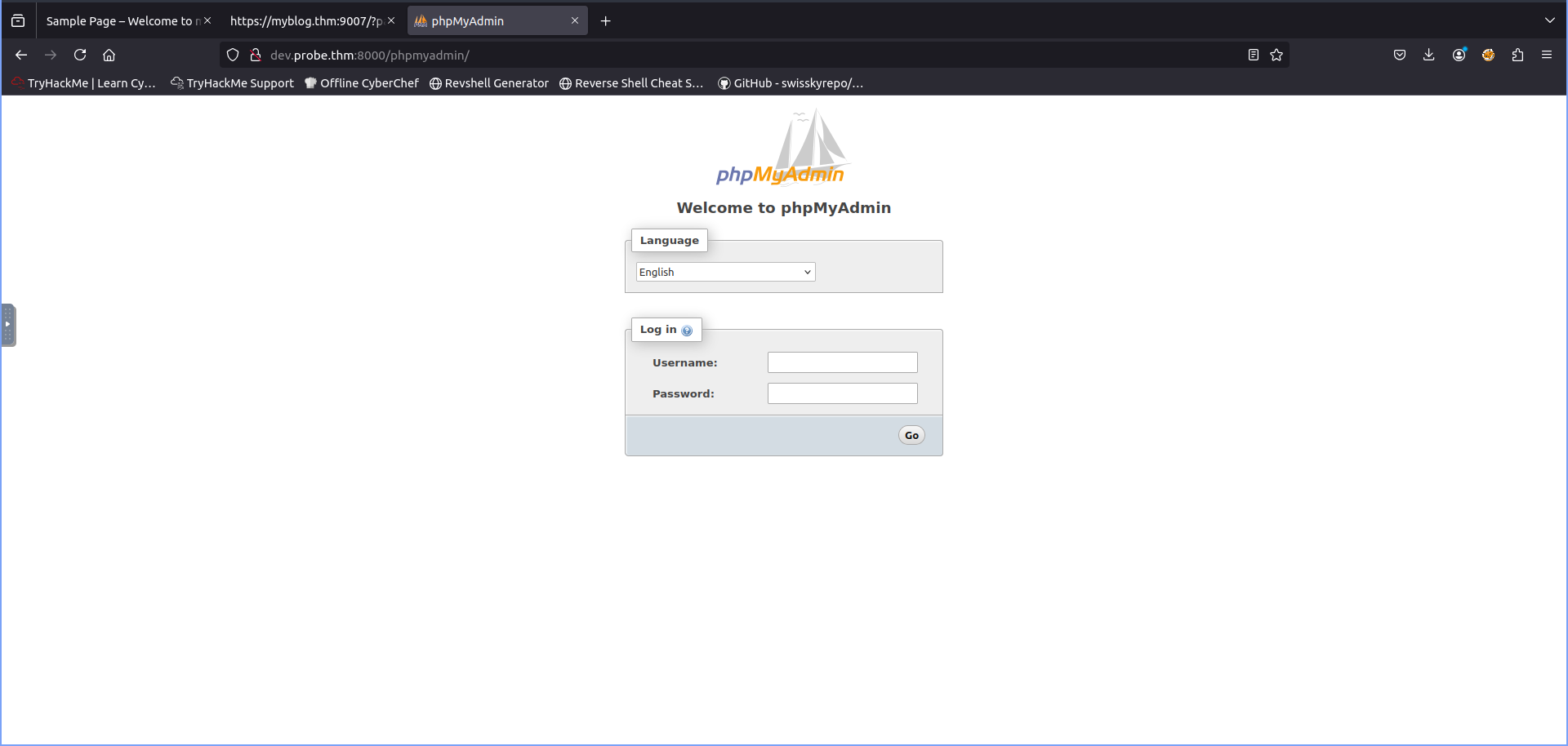
/phpmyadmin (Status: 301) [Size: 326] [--> http://dev.probe.thm:8000/phpmyadmin/]
/server-status (Status: 403) [Size: 280]
Progress: 4655 / 4656 (99.98%)
===============================================================
Finished
===============================================================
From this list of directories a few things things stood out in particular phpmyadmin this is software that allows you to manage MySQL and MariaDB databases. This is also an answer to one of the questions in the room.
Another thing that stood out was the contactus directory upon visiting this a flag was displayed. After this i began looking through the cms that was running on port 9007 viewing the source of this page i saw lats of mentions of wp and wp-includes this indicates that the CMS being used to host the blog is wordpress. Knowing this i then used wpscan to attempt to enumerate more information on the particular version being run.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
root@ip-10-10-191-190:~# wpscan --url https://10.10.205.139:9007 --disable-tls-checks
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.28
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: https://10.10.205.139:9007/ [10.10.205.139]
[+] Started: Sun Jul 13 17:00:21 2025
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.41 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: https://10.10.205.139:9007/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: https://10.10.205.139:9007/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: https://10.10.205.139:9007/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 6.2.2 identified (Insecure, released on 2023-05-20).
| Found By: Emoji Settings (Passive Detection)
| - https://10.10.205.139:9007/, Match: 'wp-includes\/js\/wp-emoji-release.min.js?ver=6.2.2'
| Confirmed By: Meta Generator (Passive Detection)
| - https://10.10.205.139:9007/, Match: 'WordPress 6.2.2'
[+] WordPress theme in use: twentytwentythree
| Location: https://10.10.205.139:9007/wp-content/themes/twentytwentythree/
| Last Updated: 2024-11-13T00:00:00.000Z
| Readme: https://10.10.205.139:9007/wp-content/themes/twentytwentythree/readme.txt
| [!] The version is out of date, the latest version is 1.6
| [!] Directory listing is enabled
| Style URL: https://10.10.205.139:9007/wp-content/themes/twentytwentythree/style.css
| Style Name: Twenty Twenty-Three
| Style URI: https://wordpress.org/themes/twentytwentythree
| Description: Twenty Twenty-Three is designed to take advantage of the new design tools introduced in WordPress 6....
| Author: the WordPress team
| Author URI: https://wordpress.org
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 1.1 (80% confidence)
| Found By: Style (Passive Detection)
| - https://10.10.205.139:9007/wp-content/themes/twentytwentythree/style.css, Match: 'Version: 1.1'
[+] Enumerating All Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:00 <====================================================================================================================================> (137 / 137) 100.00% Time: 00:00:00
[i] No Config Backups Found.
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Sun Jul 13 17:00:31 2025
[+] Requests Done: 168
[+] Cached Requests: 5
[+] Data Sent: 43.934 KB
[+] Data Received: 197.085 KB
[+] Memory used: 270.57 MB
[+] Elapsed time: 00:00:09
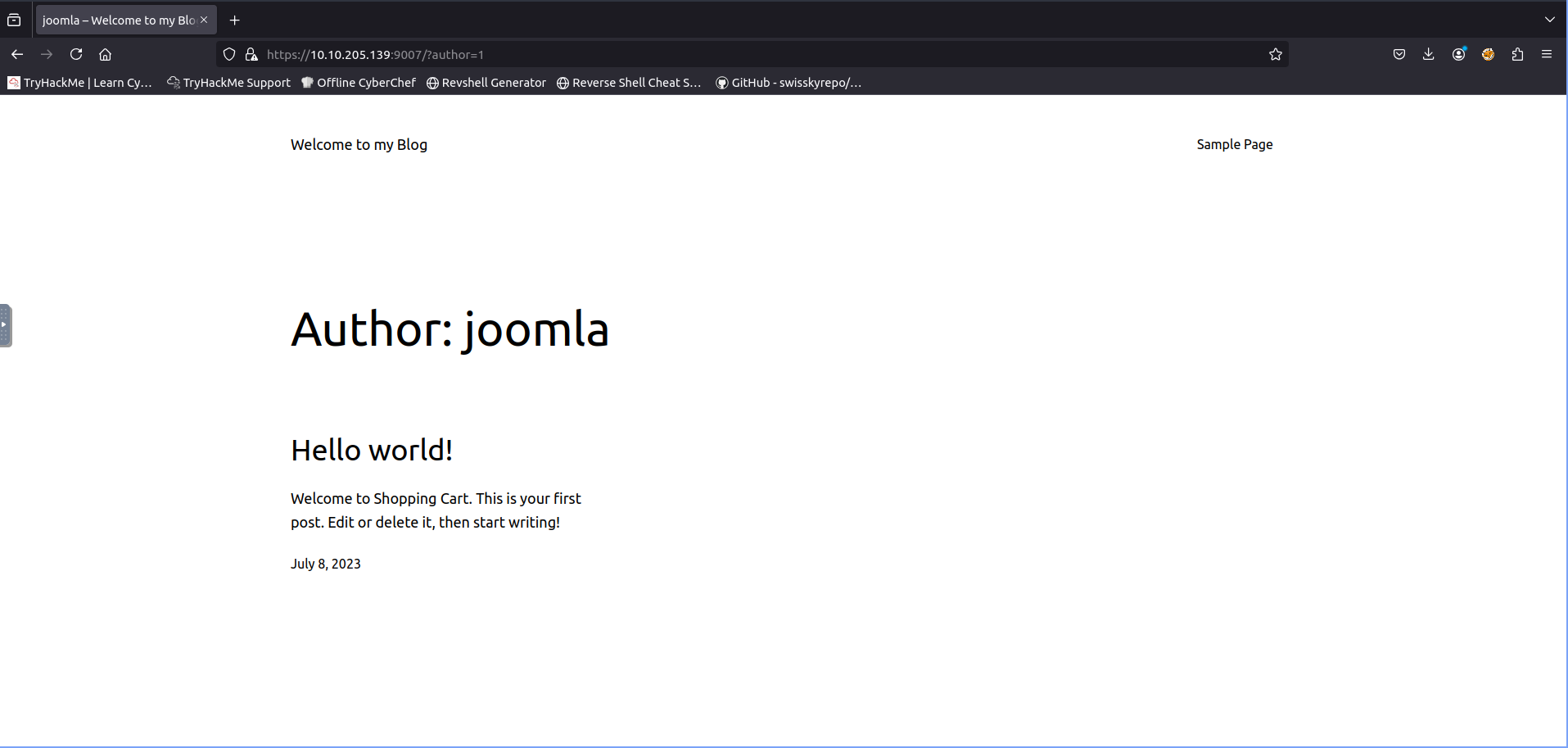
From this we can see it is running wordpress version 6.2.2. Now we need to find the username of the admin by looking at their archive page this will request the user with the id of 1’s archive page. https://10.10.205.139:9001/?author=1.
From here we can clearly see his username joomla. The next question asks us what file was detected during vulnerability scanning that can be used to identify the blogging site software with id OSVDB-3092. To do this we will need to use nikto.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
root@ip-10-10-219-8:~/nikto-master/program# perl nikto.pl -h https://10.10.205.139:9007
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 10.10.205.139
+ Target Hostname: 10.10.205.139
+ Target Port: 9007
---------------------------------------------------------------------------
+ SSL Info: Subject: /C=US/ST=Some-State/O=Internet Widgits Pty Ltd/CN=myblog.thm/emailAddress=[email protected]
Ciphers: TLS_AES_256_GCM_SHA384
Issuer: /C=US/ST=Some-State/O=Internet Widgits Pty Ltd/CN=myblog.thm/emailAddress=[email protected]
+ Start Time: 2025-07-13 17:29:59 (GMT1)
---------------------------------------------------------------------------
+ Server: Apache/2.4.41 (Ubuntu)
+ /: Link header(s) found with value(s): <https://myblog.thm:9007/index.php?rest_route=/>; rel="https://api.w.org/". See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Link
+ /: The site uses TLS and the Strict-Transport-Security HTTP header is not defined. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Strict-Transport-Security
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ /index.php?: Uncommon header(s) 'x-redirect-by' found, with contents: WordPress.
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /: The Content-Encoding header is set to "deflate" which may mean that the server is vulnerable to the BREACH attack. See: http://breachattack.com/
+ /: Suggested security header missing: content-security-policy. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/CSP
+ /: Suggested security header missing: permissions-policy. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Permissions-Policy
+ /: Suggested security header missing: x-content-type-options. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Content-Type-Options
+ /: Suggested security header missing: strict-transport-security. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Strict-Transport-Security
+ /: Suggested security header missing: referrer-policy. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Referrer-Policy
+ Apache/2.4.41 appears to be outdated (current is at least 2.4.63). Apache 2.2.34 is the EOL for the 2.x branch.
+ Hostname '10.10.205.139' does not match certificate's names: myblog.thm. See: https://cwe.mitre.org/data/definitions/297.html
+ /: Web Server returns a valid response with junk HTTP methods which may cause false positives.
+ /phpmyadmin/changelog.php: Cookie goto_https created without the httponly flag. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Cookies
+ /phpmyadmin/changelog.php: Cookie back_https created without the httponly flag. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Cookies
+ /phpmyadmin/changelog.php:X-Frame-Options header is deprecated and was replaced with the Content-Security-Policy HTTP header with the frame-ancestors directive instead. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /phpmyadmin/changelog.php: Uncommon header(s) 'x-ob_mode' found, with contents: 1.
+ /wp-links-opml.php: This WordPress script reveals the installed version.
+ /license.txt: License file found may identify site software.
+ /: A Wordpress installation was found.
+ /phpmyadmin/: phpMyAdmin directory found.
+ /wp-login.php?action=register: Cookie wordpress_test_cookie created without the httponly flag. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Cookies
+ /wp-login.php: Wordpress login found.
+ 8084 requests: 0 error(s) and 23 item(s) reported on remote host
+ End Time: 2025-07-13 17:30:56 (GMT1) (57 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Now unfortunately it does link to the osvdb code but we can see from this line + /license.txt: License file found may identify site software. that the file the question asks for is license.txt. osvdb is no longer active.
The final question asks what is the name of the software beging used on the standard http port this can be seen from our initial nmap scan as lighttpd.